Headers
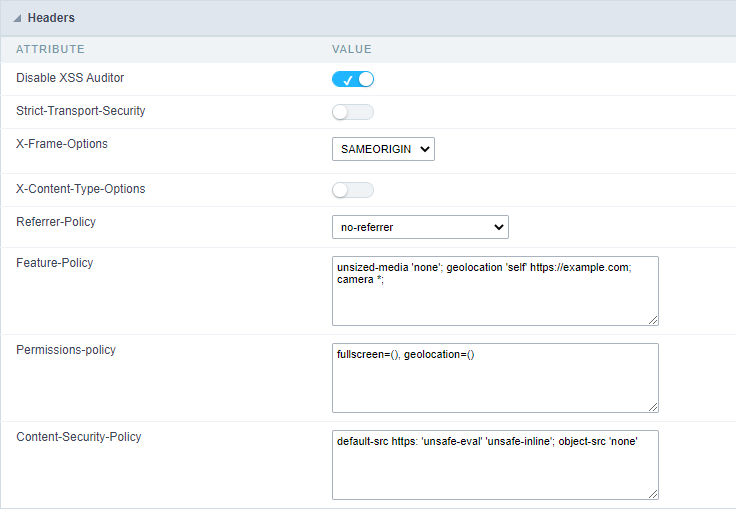
Disable XSS Auditor
XSS is short for Cross-Site Scripting, which is an attack that consists of sending HTML with malicious JavaScript to a website.
It is a security attack that consists of sending HTML with malicious JavaScript to a website. If the website displays this HTML with JavaScript without filtering the malicious JavaScript code, the cookies sent by the website can be stolen and sent to an attacking website, so that it can be used to forge user sessions and access the website’s user account without permissions.
Strict-Transport-Security
HSTS forces browsers to use HTTPS in the domain where it is enabled, instead of using HTTP.
When enabled, the default value is “max-age = 31536000”.
The HSTS policy is set for one year (31536000 seconds). This period specifies the time the browser will access the server via HTTP
X-Frame-Options

The HTTP X-Frame-Options response header can be used to indicate whether or not the browser should render the page in a <frame>, `<iframe>` `,` < embed> '' or
X-Frame-Options does not allow the rendering of a page in a frame, ensuring that the content of your page is not embedded in other sites
- SAMEORIGIN: The SAMEORIGIN directive allows the page to be loaded in a frame from the same source as the page itself. This option must be used so that the application with clickjacking protection can be used in the menu application.
- DENY: This directive completely disables page loading in a frame.
If no option is selected, the application can be used on any
`<frame>`,<iframe>`,`or`<object>, allowing the application to be incorporated into another website.
X-Content-Type-Options
X-Content-Type-Options is used to protect against MIME detection vulnerabilities. With this option enabled, it prevents browsers from interpreting the page content (sniffing) and executing the data as code / tag. These vulnerabilities can occur when uploading a text file with a javascript code and the browser reading the content that is in the file and executing, even though it is just text and not part of the code.
With this enabled, the HTTP X-Content-Type-Options header is defined, by default, as “no detection”.
Referrer-Policy
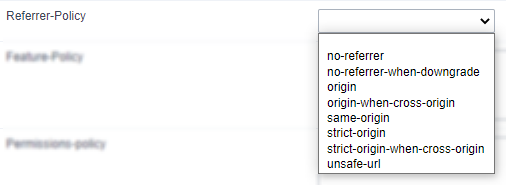
no-referrer.
The Referer header will be omitted completely. No reference information will be sent with requests.
no-referrer-when-downgrade.
This is the default behavior when no policy is specified, or if the value provided is invalid.
origin.
Only send the origin of the document as a reference. For example, a document at https://example.com/page.html will send the reference https://example.com/.
origin-when-cross-origin.
Sends the origin, path and query string when performing a same-origin request, but only sends the origin of the document in other cases.
same-origin.
The reference will be sent to sources on the same site, but requests between sources will not send reference information.
strict-origin.
Only send the document source as a reference when the security protocol level remains the same (HTTPS → HTTPS), but do not send it to a less secure recipient (HTTPS → HTTP).
strict-origin-when-cross-origin.
Sends the source, path and query string when performing a request from the same source, only sends the source when the security protocol level remains the same during an inter-source request (HTTPS → HTTPS), and sends no header to recipients less secure (HTTPS → HTTP)
unsafe-url.
Sends the source, path and query chain when performing any request, regardless of security.
Feature-Policy
The value of this header is a policy or set of policies that you want the browser to respect for a particular source.
The source whitelist can take on several different values:
`*:`The feature is allowed in top-level navigation contexts and in nested navigation contexts (iframes).`'self':`The feature is allowed in top-level navigation contexts and nested navigation contexts from the same source. It is not allowed in documents of cross origin in nested browsing contexts.`'none':`The feature is not allowed in top-level browsing contexts and is not allowed in nested browsing contexts.`<origin (s)>:`specific sources for which to enable the policy (for example https://example.com).
Example 1 - Using only one directive Let’s say you want to prevent all content from using the geolocation API on your site. You can do this by submitting a restricted ‘none’ whitelist to the geolocation resource:
Feature-Policy: `geolocation 'none'`
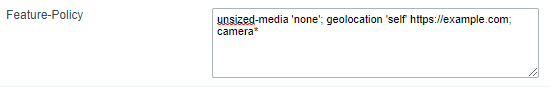
Example 2 - Using more than one directive Functionalities within a policy are separated by semicolons.
Feature-Policy: unsized-media 'none'; geolocation 'self' https://example.com; camera *; `
Directives
accelerometer
Controls whether the current document is allowed to collect information about the acceleration of the device via the Accelerometer interface.
ambient-light-sensor
Controls whether the current document is allowed to collect information about the amount of light in the environment around the device through the AmbientLightSensor interface.
autoplay
Controls whether the current document is allowed to play the requested media automatically via the HTMLMediaElement interface. When this policy is disabled and there is no user action, the Promise returned by HTMLMediaElement.play () will reject it with a DOMException. The autoplay attribute on <audio> '' and
battery
Controls whether the use of the Battery Status API is allowed. When this policy is disabled, the Promise returned by Navigator.getBattery () will reject it with a NotAllowedError DOMException.
camera
Controls whether the current document is allowed to use inputs from video devices. When this policy is disabled, the Promise returned by getUserMedia () will reject it with a NotAllowedError DOMException.
display-capture
Controls whether or not the current document is allowed to use the getDisplayMedia () method to capture screen content. When this policy is disabled, the Promise returned by getDisplayMedia () will reject it with a NotAllowedError if permission is not obtained to capture the contents of the screen.
document-domain
Control whether the current document is allowed to place document.domain. When this policy is disabled, attempts to place document.domain will fail and cause a SecurityError DOMException to be thrown.
encrypted-media
Controls whether the current document is allowed to use the Encrypted Media Extensions (EME) API. When this policy is disabled, the Promise returned by Navigator.requestMediaKeySystemAccess () will reject it with a DOMException.
execution-while-not-rendered
Controls whether tasks should be performed in frames while they are not rendered (e.g. whether a frame is hidden or display: none).
execution-while-out-of-viewport
Controls whether tasks should be performed in frames while they are outside the visible viewing window.
fullscreen
Controls whether the current document is allowed to use Element.requestFullScreen (). When this policy is disabled, the returned Promise rejects it with a TypeError DOMException.
geolocation
Controls whether the current document is allowed to use the Geolocation interface. When the policy is disabled, calls to getCurrentPosition () and watchPosition () will cause function callbacks to be invoked with a PositionError of PERMISSION_DENIED.
gyroscope
Controls whether the current document is allowed to collect information about the orientation of the device through the Gyroscope interface.
layout-animations
Controls whether the current document is allowed to show layout animations.
legacy-image-formats
Controls whether the current document is allowed to show images in legacy formats.
magnetometer
Controls whether the current document is allowed to collect information about the orientation of the device through the Magnetometer interface.
microphone
Controls whether the current document is allowed to use inputs from audio devices. When this policy is disabled, the Promise returned by MediaDevices.getUserMedia () will reject it with a NotAllowedError.
midi
Controls whether the current document is allowed to use the Web MIDI API. When this policy is disabled, the Promise returned by Navigator.requestMIDIAccess () will reject it with a DOMException.
navigation-override
Controls the availability of mechanisms that enable the author of the page to take control over the behavior of spatial navigation, or to cancel completely.
oversized-images
Controls whether the current document is allowed to download and display large images.
payment
Controls whether the current document allows the use of the Payment Request API. When this policy is disabled, the PaymentRequest () constructor will throw a SecurityError DOMException.
picture-in-picture
Controls whether the current document allows a video to be allowed to play in Picture-in-Picture mode via the corresponding API.
publickey-credentials-get
Controls whether the current document is allowed to use the Web Authentication API to retrieve already stored public key credentials, i.e. via navigator.credentials.get ({publicKey: …, …}).
sync-xhr
Controls whether the current document is allowed to make synchronous XMLHttpRequest requests.
usb
Controls whether the current document is allowed to use the WebUSB API.
vr
Controls whether the current document is allowed to use the WebVR API. When this policy is disabled, the Promise returned by Navigator.getVRDisplays () will reject it with a DOMException. Keep in mind that the WebVR standard is in the process of being replaced by WebXR.
wake-lock
Controls whether the current document is allowed to use the Wake Lock API to indicate that the device should not go into a power saving mode.
screen-wake-lock
Controls whether the current document is allowed to use the Screen Wake Lock API to indicate whether or not the device should darken the screen.
xr-spatial-tracking
Controls whether or not the current document is allowed to use the WebXR Device API to interact with the WebXR session.
Content-Security-Policy
Content-Security-Policy is the name of an HTTP response header that modern browsers use to increase the security of the document (or web page).
The Content-Security-Policy header allows you to restrict resources such as JavaScript, CSS or just about anything the browser loads.
Directives
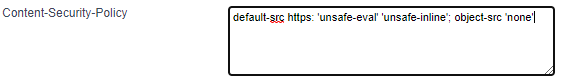
default-src
The default-src directive defines the standard policy for fetching features such as JavaScript, Images, CSS, Fonts, AJAX requests, Frames, HTML5 Media. Not all directives go back to default-src. Refer to the Source List Reference for possible values.
DFAULT-SRC Policy Example
default-src 'self' cdn.example.com;
script-src
Defines valid JavaScript sources.
SCRIPT-SRC Policy Example
script-src 'self' js.example.com;
style-src
Defines valid fonts for style sheets or CSS.
EXAMPLE__ STYLE-SRC POLICY
style-src 'self' css.example.com;
img-src
Defines valid image sources.
Example of IMG-SRC Policy
img-src 'self' img.example.com;
connect-src
Applies to XMLHttpRequest (AJAX), WebSocket, fetch (), `<a ping> '' 'or EventSource. If not allowed, the browser emulates a 400 HTTP status code.
__Connect-SRC Policy Example__
connect-src ‘self’; ‘’
font-src
Defines valid fonts for font resources (loaded via @ font-face).
FONT-SRC Policy Example
font-src font.example.com; `
object-src
Defines valid plug-in sources, for example `<object>` `,` `or` <applet> ``.
__ OBJECT-SRC Policy Example__ `` object-src ‘self’; ‘’
media-src
Defines valid audio and video sources, for example <audio> , HTML5, <video> `` elements.
Example of MEDIA-SRC Policy
media-src media.example.com;
frame-src
Defines valid fonts for loading frames. In CSP, Level 2 frame-src has been deprecated in favor of the child-srcdirective. CSP Level 3, has not been replaced with frame-src and will continue to postpone child-src if not present.
Example FRAME-SRC `` frame-src ‘self’; ‘’
sandbox
Enables a sandbox for the requested resource similar to the iframe sandbox attribute. The sandbox applies a policy of the same origin, avoids pop-ups, plug-ins and blocks the execution of scripts. You can keep the sandbox value empty to keep all restrictions in place, or add values: allow-forms allow-same-origin allow-scripts allow-popups, allow-modals, allow-orientation-lock, allow-pointer-lock, allow-presentation, allow-popups-to-escape-sandbox, eallow-top-navigation
Example of SANDBOX policy
sandbox allow-forms allow-scripts;
report-uri
Instructs the browser to POST policy crash reports to this URI. You can also use Content-Security-Policy-Report-Only as the HTTP header name to instruct the browser to send reports only (does not block anything). This directive was discontinued at CSP Level 3 in favor of the report-todirective.
Example REPORT-URI
report-uri / some-report-uri;
child-src
Defines valid fonts for web workers and nested browsing contexts loaded using elements such as <frame> '' and <iframe> ``
Example of FILHO-SRC Policy
child-src 'self'
form-action
Defines valid fonts that can be used as an `<form>` HTML action.
Example action policy example `` form-action ‘self’; ‘’
frame-ancestors
Defines valid fonts for embedding the resource using `<frame> <iframe> <object> <embed> <applet>`. Setting this directive to ‘none’ should be roughly equivalent to X-Frame-Options: DENY
FRAME-ANCESTORS__ EXAMPLE POLICY
frame-ancestors ‘none’;
plugin-types
Defines valid MIME types for plug-ins called via <object> and `<embed>`. To load one, `` <applet> ‘’ you must specify application / x-java-applet.
PLUG-IN TYPES Policy Example
`plugin-types application / pdf;`
base-uri
Defines a set of allowed URLs that can be used in the attribute of an HTML basetag.
URI-BASE Policy Example `` base-uri ‘self’; ‘’
report-to
Defines a report group name defined by an HTTP Response Report-Header. See the reporting API for more information.
Example Report for Policy
report-to groupName;
worker-src
Restricts URLs that can be loaded as Worker, SharedWorker or ServiceWorker.
WORKER-SRC Policy Example
worker-src 'none'; `
manifest-src
Restricts URLs where application manifests can be loaded.
Example of MANIFEST-SRC Policy
manifest-src 'none'; `
prefetch-src
Defines valid sources for pre-fetching and pre-rendering of requests, for example, through the linktag with rel = “prefetch” or rel = “prerender”:
__ PREFETCH-SRC Policy Example__
prefetch-src 'none'`
navigate-to
Restricts the URLs to which the document can navigate by any means. For example, when a link is clicked, a form is submitted or window.location is called. If form-action is present, this directive will be ignored for submitting forms. Implementation status
Navigation Policy Example
`navigate-to example.com`
