General
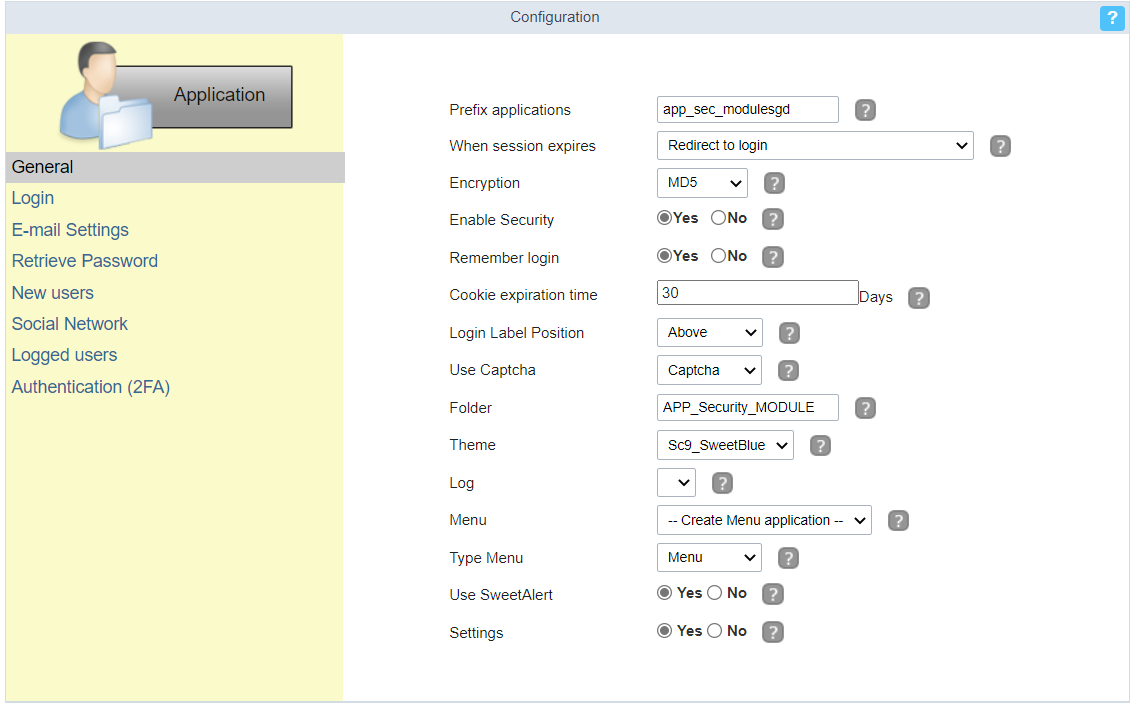
Applications Prefix
You can set a prefix to the application names of the Security Module.
When session expires
Define the behaviour when the session expires.
- No action - The user continues using the application, but no saves after the session expires.
- Redirect to login after the session expiration - The application returns to the login after expiring the session.
- Display a message that the session has expired - Shows the message “session has expired” to the user.
Encryption
Use encryption to store the password in the table of users.
Enable Security
Activate the flag Application Security for all project applications.
Remember login
Activating the flag allows the user to remain logged in when returning to the system when the session ends, without having logged out.
Cookie expiration time
Cookie expiration time in days for Remember login option
Label Position at Login
Defines the Label positioning of the fields in relation to the data.
- Beside - Default value of the applications, placing the label on the right side of the input label to the Side
- Above - Positions the label above the input label Above
- Below - Positions the label below the input label Below
- Watermark - Positions the label as Watermark.
Enable Captcha
It activates the captcha for the login application.
- No - Does not display the captcha in the login application.
- Captcha - Uses the built-in scriptcase library for captcha display.
- reCAPTCHA - Uses Google’s reCAPTCHA V2. To configure, click here.
Watch a video of reCAPTCHA. If you prefer, see a tutorial on how to generate the keys.
Site Key
Key generated by Google after reCAPTCHA project creation.
Secret Key
Key generated by Google after reCAPTCHA project creation.
Folder
The project folder name to store the applications generated by Security Module.
Theme
The theme to create the Security Module applications.
Log
This option is available if the project already has a Log Module.
Click here and check out how to create a Log Module
Menu
This option is only available if your project already has a Menu Application. You can associate the existing Menu and include all applications generated by the Security Module to it. If you do not select an existing Menu here, it creates a new Menu Application.
Menu Type
Security Module menu type (option only available if you do not select an existing menu in the previous item)
This option is available when using the Create Application Menu option in the menu item
Use SweetAlert
Enables the use of sweetAlert in security module applications.
Settings
Defines whether the security module editing application will be generated.
With this option active, the system administrator user will be able to change some settings of the security module at the end, when accessing the system.
See below for the list of options available for editing the security module.
- Action for session expiration - Define the system behavior when the session expires. This feature is triggered as soon as a new action is performed.
- No action: No action will be taken and the user will continue using the system, however no action will be saved.
- Redirect to login: When performing some action on the system, the user will be redirected to the login application.
- Displays a message and redirects to login: or perform some action on the system, a message will be displayed informing you that the session has expired with an ok button. By clicking on the button, the user will be redirected to the login application.
- Remember login - Activating the flag allows the user to remain logged in when returning to the system when the session ends, without having logged out.
- Remember login expiration time - Cookie expiration time in days for the Remember login option. By default, Scriptcase sets the limit to 30 days.
- Recover Password - Enables the reset password button on the login screen.
- New Users - Enables the add new users button on the login screen.
- Brute force - Enables or disables the failed access attempt limit.
- Block time for Brute Force protection - Defines the time, in minutes, that the user will remain unreachable after several failed login attempts.
- Brute Force Attempts for blocking - Defines the number of failed access attempts until protection is activated.
- 2F - Defines whether two-factor authentication will be used on the system.
- 2FA Expiration Time - Determines the time in seconds that the 2FA authentication token will expire
